Greenhouse will be deactivating support for TLS v1.0 across our public facing applications. We are providing you advanced notice so that our customers and partners can prepare accordingly. If you are using unsupported clients to connect to Greenhouse after deactivating TLS v1.0, you will begin receiving connection error messages.
Why are we deactivating TLS v1.0?
We are deactivating TLS v1.0 to ensure that Greenhouse software is providing our customers and partners with the safe and secure protocols for our connections. This change is enforced throughout the industry to maintain secure connections that encrypt and protect your sensitive data from malicious breaches. The PCI Security Standards Council updated their guidance and will now require full deprecation of TLS 1.0 on June 30th, 2018 for applications that process payments. Although, we only support payments on the Recruiting application, we will be following the recommendation across all our inbound connections.
Am I affected?
Greenhouse has done some initial analysis and the deactivating of TLS v1.0 should only affect < 1% of our total traffic. There are two major categories of user’s that could be affected by the deprecation of TLS v1.0:
1. Customers and end-users using browsers or mobile applications
This includes customers using unsupported browsers to access the Greenhouse Recruiting and Onboarding applications as well as job applicants accessing job boards hosted by Greenhouse.
Supported Browsers
You can use the following website to easily determine if your browser supports a version of TLS > v1.0.
https://www.ssllabs.com/ssltest/viewMyClient.html
| Browser Version | Notes |
| Android 5.0 (Lollipop) and up | Supported by default |
| Android 4.4 (KitKat) to 4.4.4 |
Some devices are supported Go to https://www.ssllabs.com/ssltest/viewMyClient.html from your device browser to determine compatibility. |
| Chrome 38 and up | Supported by default |
| Chrome 22-27 | Supported when running on Windows XP SP3, Vista, or newer, OS X 10.6 (Snow Leopard) or newer, or Android 2.3 (Gingerbread) or newer. |
| Firefox 27 and up | Supported by default |
| Firefox 23-26 | Supported only after configuration: Browser to about:config and update ‘security.tls.version.max’ to 2 |
| Internet Explorer 11 (Desktop and mobile) | Supported by default |
| Microsoft Edge | Supported by default |
| Safari 7 and up on OS X 10.9 (Mavericks) and up | Supported by default |
| Mobile Safari 5 and up for iOS 5 and up | Supported by default |
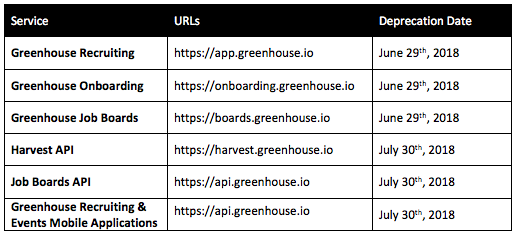
2. Customers using HTTP clients to connect to our Harvest and Job Boards API
Customers that have custom clients and are using clients that do not support TLS v1.1 and above will no longer be able to successfully connect to our Harvest and Job Boards API.
Customer should ensure that they are using a support client or else it will lead to downtime of any internal processes that utilize the Harvest API or any Job boards that are built using our Job Boards API.
Greenhouse will be performing analysis of connections to our Harvest and Job Boards API and performing proactive communications to affected customer to ensure a smooth transition. We still recommend that our customers do not rely solely on us and each customer that utilizes these APIs should ensure that they are prepared for the deprecation date.
You can use the following API to easily test the library you are using for API connections to Greenhouse to ensure it supports TLS v1.1 or greater.
https://www.howsmyssl.com/a/check
The HTTP response will contain a ‘tls_version’ value which contains the highest version of TLS that is supported by the client.
See below for a list of common clients that may be used as an HTTP client to our API:
| Clients | Notes |
| OpenSSL 1.0.1 and up |
Most HTTP clients available in languages will be using the OpenSSL client to initiate TLS connections Some versions of Mac OSX are shipped with v0.9.8y and would therefore no longer work. You can upgrade to a newer version of OpenSSL via the Homebrew tool. brew install openssl |
| Java version 7u26 and up |
TLS 1.1 and 1.2 must be manually enabled You will need to add the following property -Dhttps.protocols=TLSv1.1,TLSv1.2 which configures the JVM to specify which TLS protocol version should be used during https connections. |
| Java version 8 and up | Supported by default |
| Python 2.7.9 and up | Supported by default |
| Ruby 2.0.0 and up | Supported by default is the underlying OS is running OpenSSL 1.0.1 and up |