Your organization can set up single sign-on (SSO) with Active Directory Federation Services (ADFS) to authenticate users logging in to Greenhouse Onboarding and Greenhouse Welcome.
Enter your SSO credentials in Greenhouse Onboarding
Before you can configure ADFS, you'll need to provide the following information for your identity provider in Greenhouse Onboarding:
- Your Single Sign-On URL
- Your Single Logout URL (Optional)
- Your IdP Certificate Fingerprint (SHA1 format)
To do this, open Greenhouse Onboarding and navigate to Settings > Data Flow > Single Sign-On.
On the Single Sign-On page, enter your SSO URL, IdP certificate fingerprint, and single logout URL in their corresponding fields.
Click Save.
Once you've entered your SSO information, reach out to Greenhouse Technical Support to turn on your SAML configuration setup.
Before closing Greenhouse Onboarding, copy your organization's SSO Assertion Consumer URL and Entity ID/Issuer from the Single Sign-On page. You'll use these values during Step 1 of setup in ADFS.
Connect Greenhouse Onboarding to ADFS
Note: These instructions were created using Windows Server 2012 R2 and ADFS 3.0.
Step 1: Add Greenhouse Onboarding as a Relying Party Trust
To begin, navigate to your ADFS management tool.
Expand the Trust Relationships folder in the left panel, then open the Relying Party Trusts subfolder.
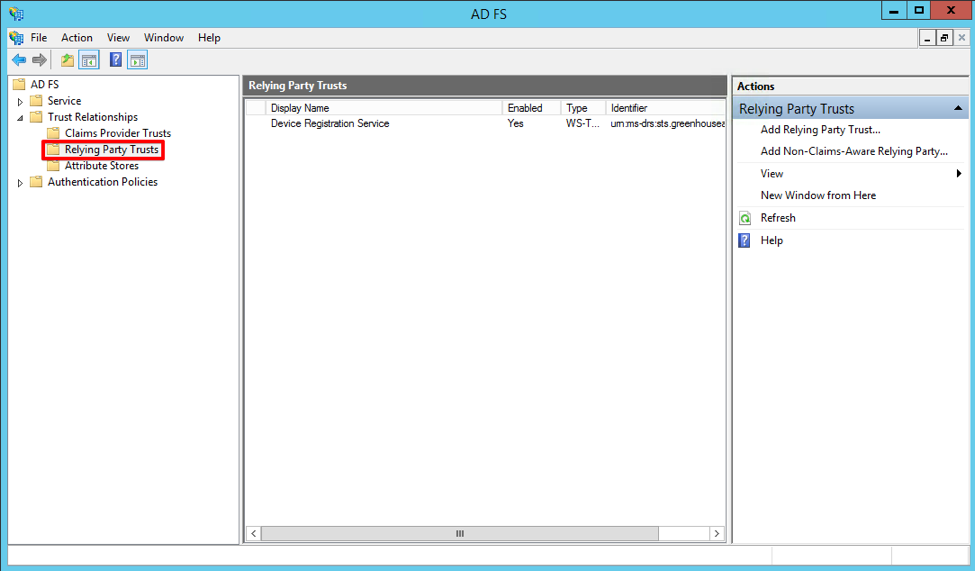
Under the Actions panel on the right, click Add Relying Party Trusts.
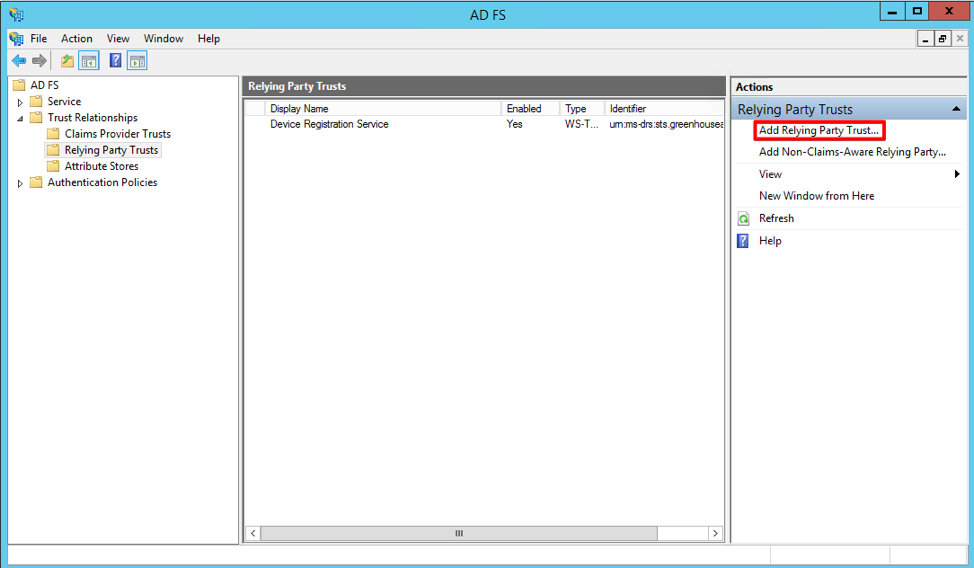
The Add Relying Party Trust Wizard will open. On the Welcome page, click Start.
On the Select Data Source page, select Enter data about the relying party manually.
Use the SSO Assertion Consumer URL and Entity ID that you retrieved from Greenhouse Onboarding. Enter your SSO Assertion Consumer URL in the SAML Assertion Consumer Endpoints field. Enter your Entity ID in the Relying party identifiers field.
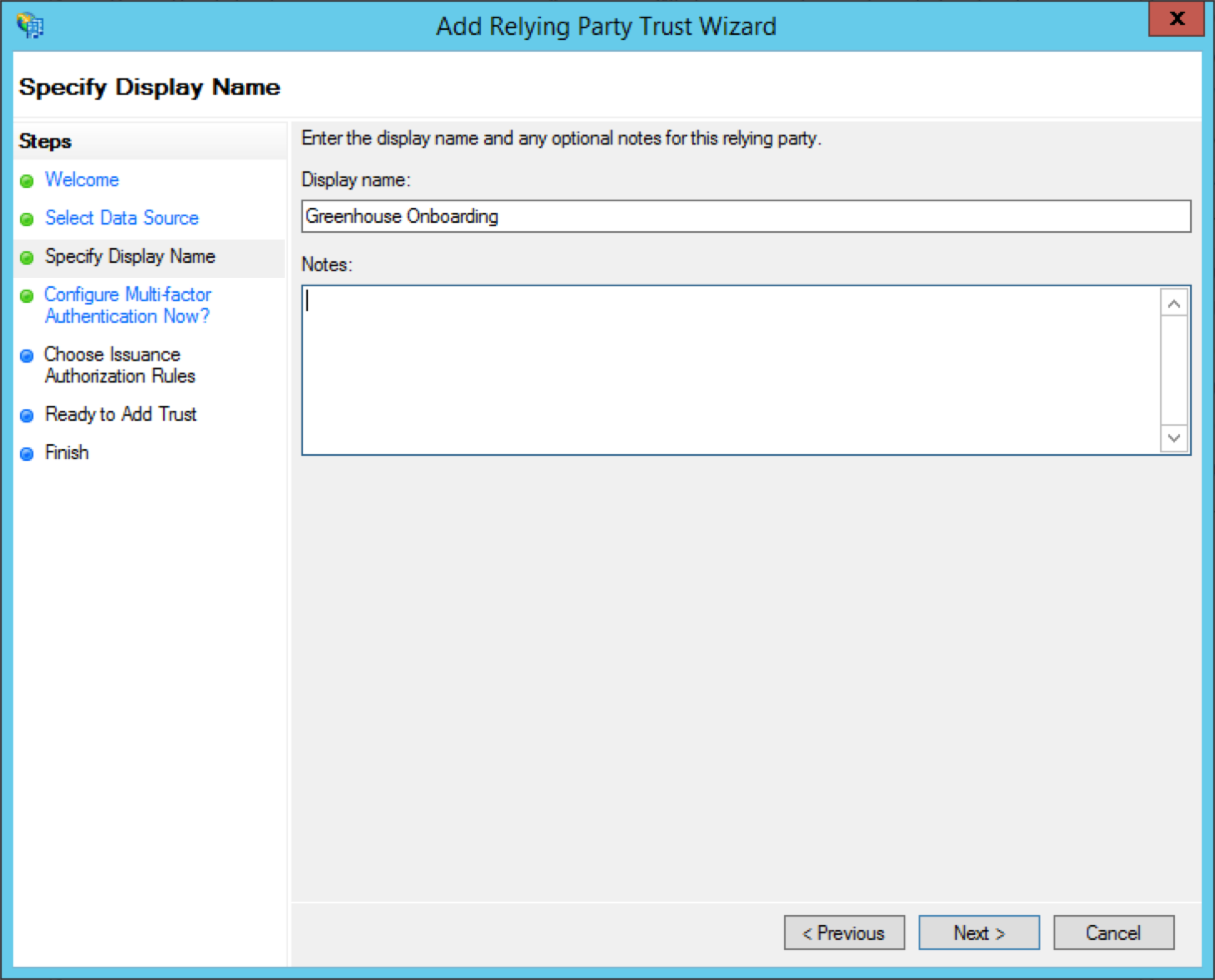
Next, enter Greenhouse Onboarding as your display name.
You can also add any additional notes that you’d like in the Notes section.
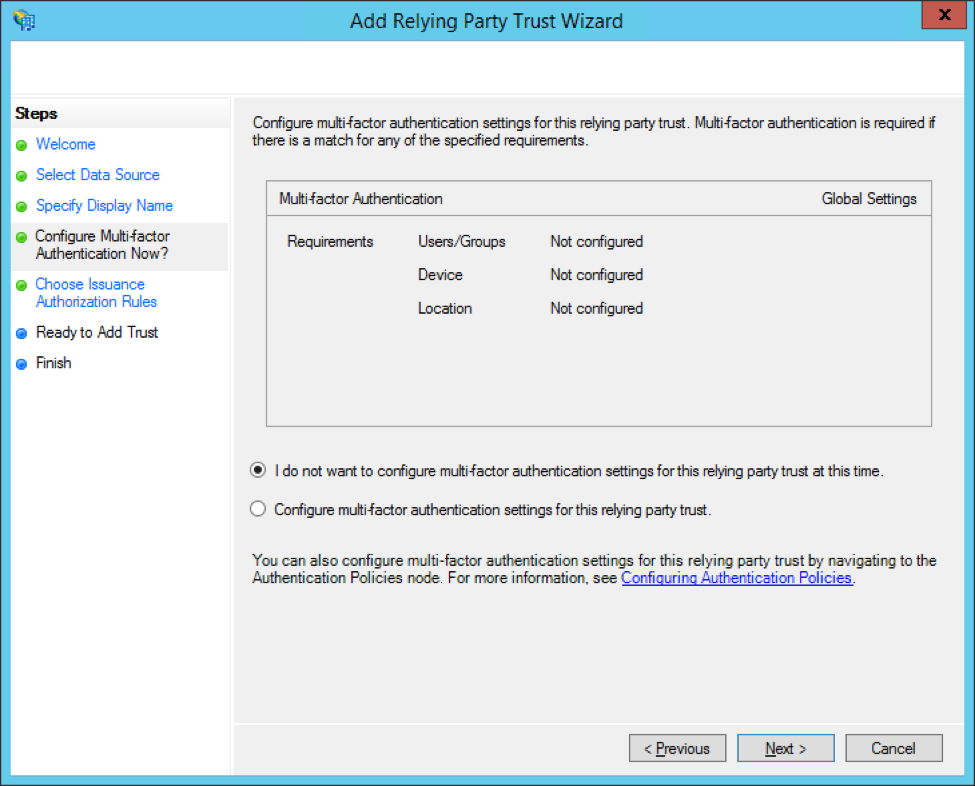
On the next page, you'll be given the option to set up multi-factor authentication. This isn't required for your Greenhouse Onboarding configuration, but you can set it up if you choose.
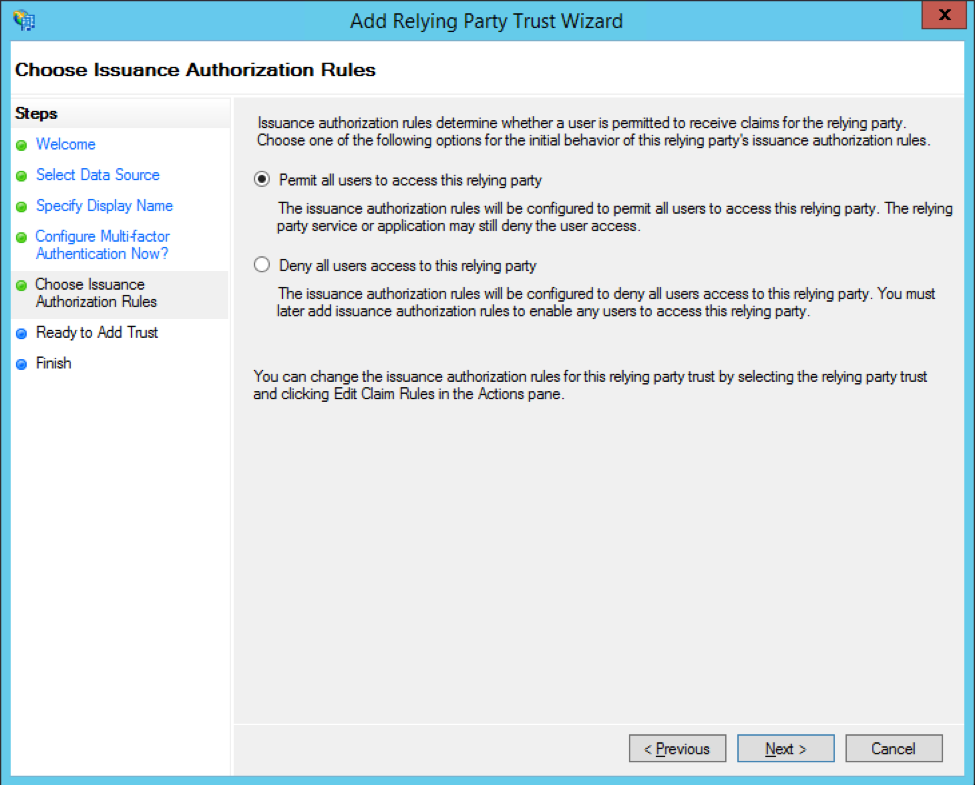
On the Choose Issuance Authorization Rules step, select Permit all users to access this relying party.
The next page will be an overview of your configuration. Confirm that the following attributes were set correctly before moving on:
The Identifiers tab contains your display name and the relying party identifier from Greenhouse Onboarding. The relying party identifier will use your subdomain and be in the format app.parklet.co.
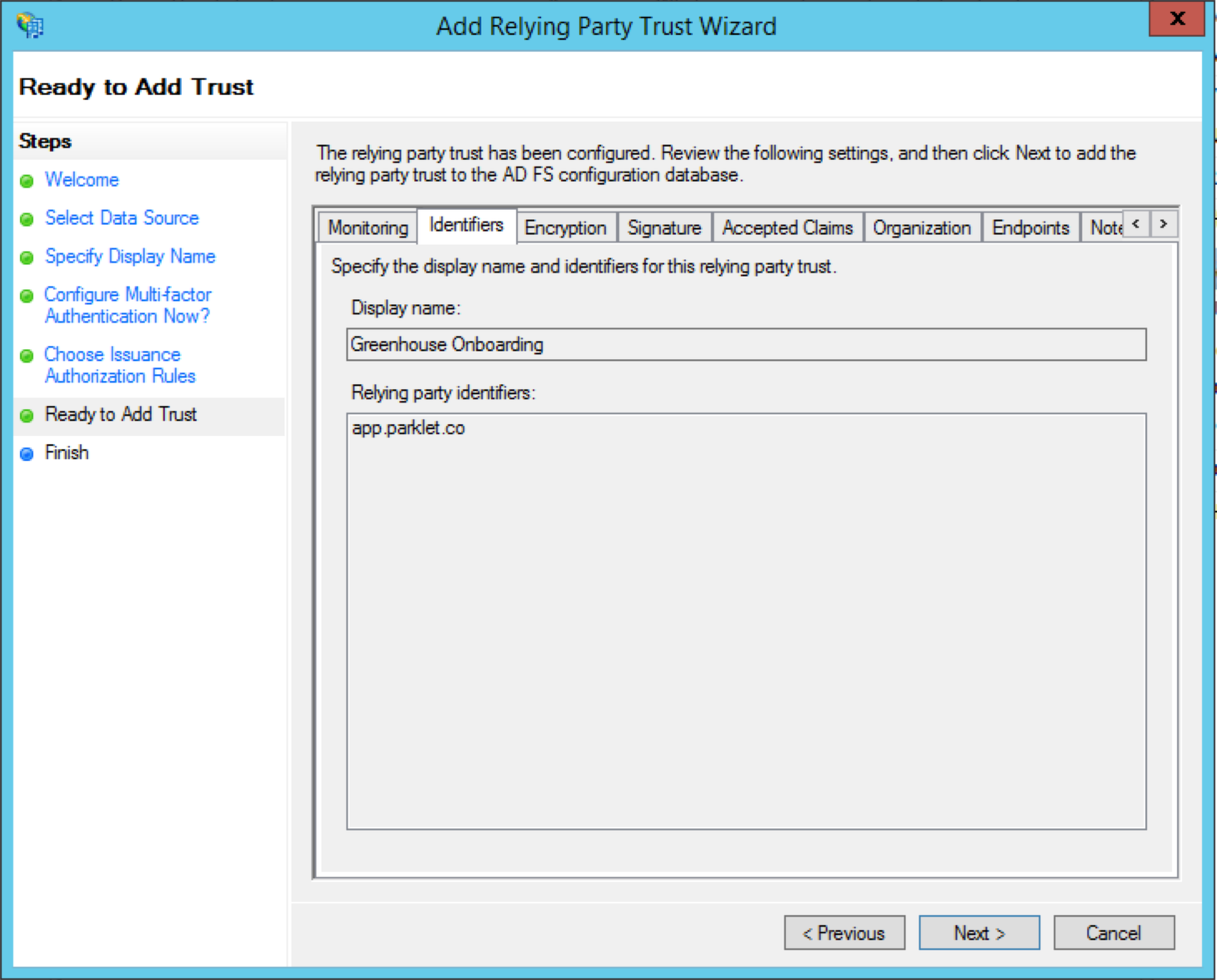
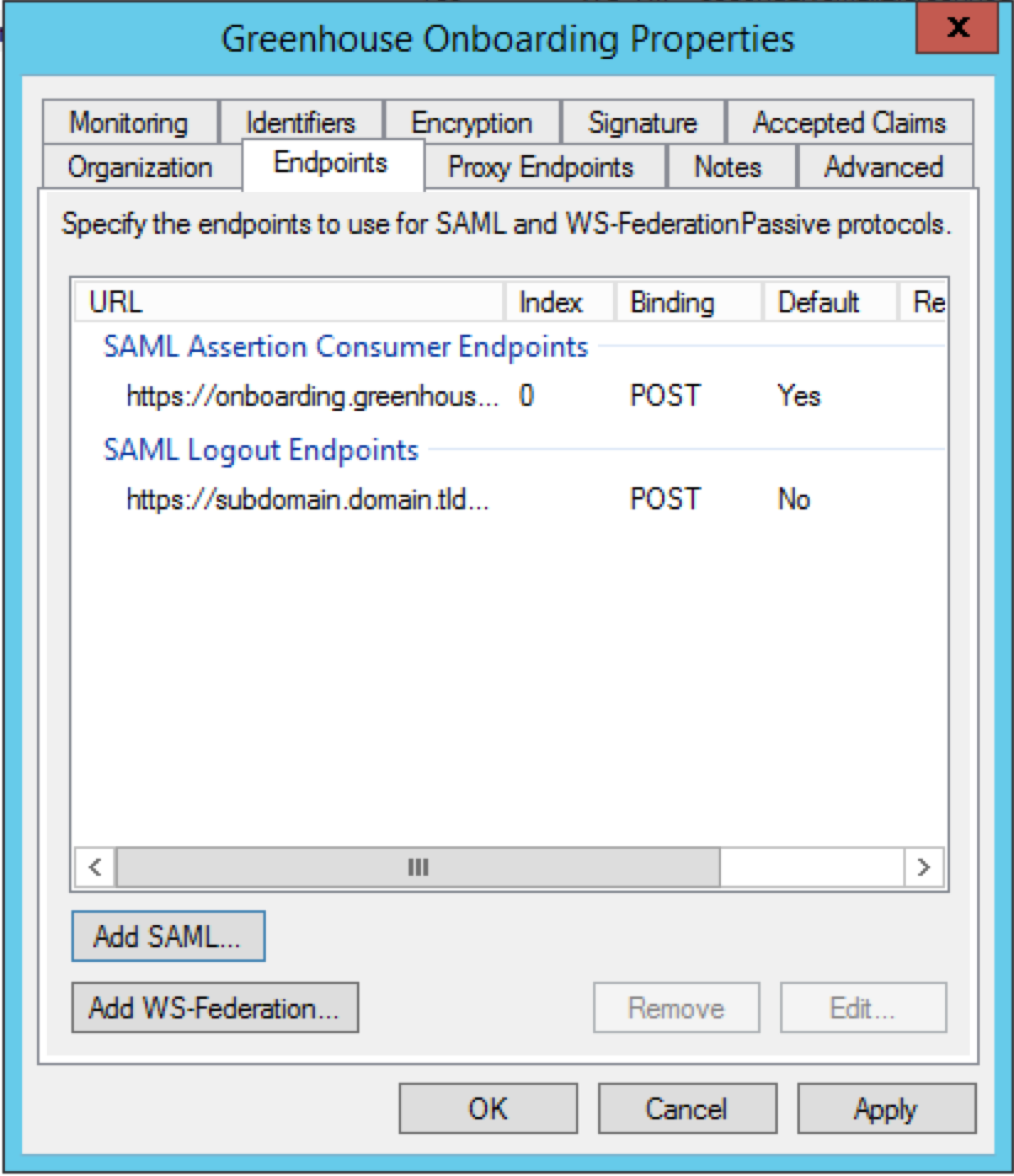
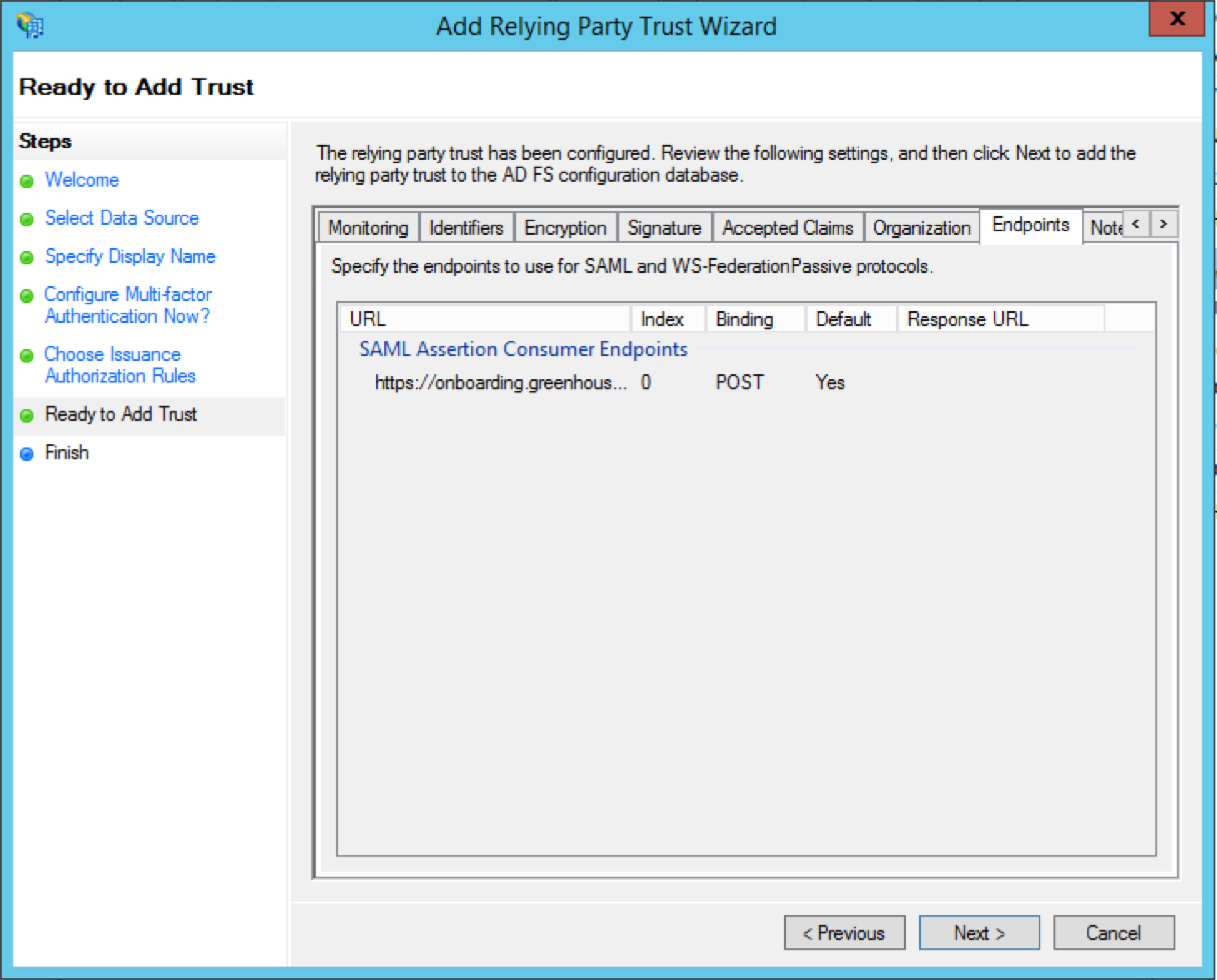
The Endpoints tab contains your SAML Assertion Consumer Endpoint from Greenhouse Onboarding. Your URL should be in the format https://onboarding.greenhouse.io/saml/{uid}/consume, with your organization's UID populated.
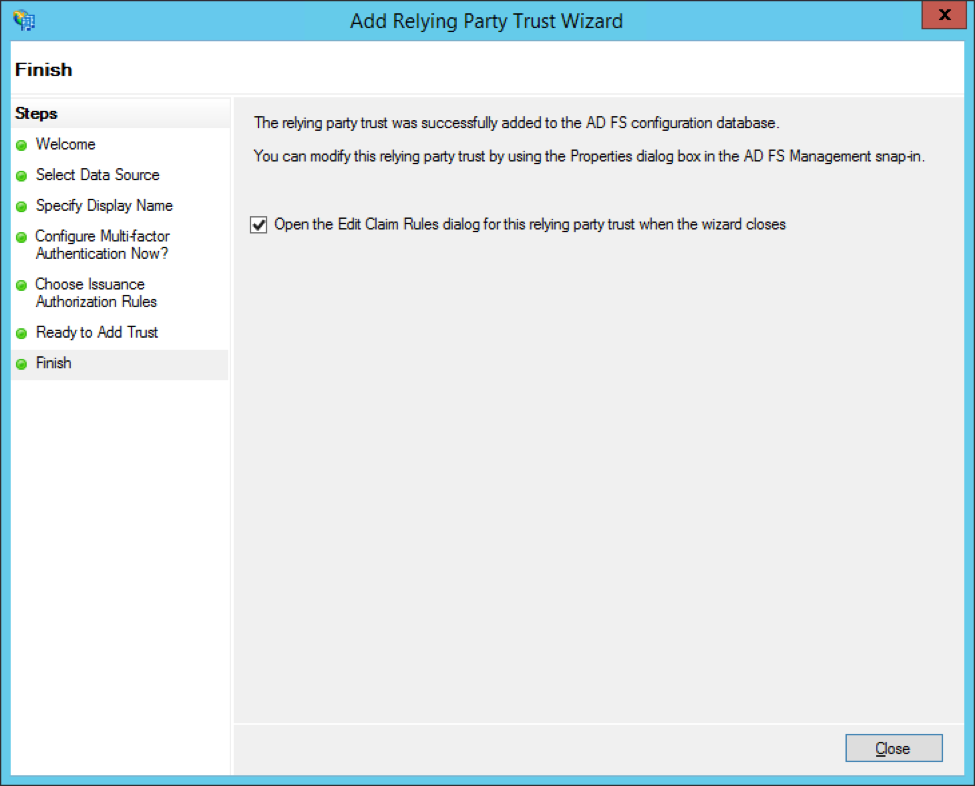
On the next page, mark the checkbox Open the Edit Claim Rules dialog for this relying party trust when the wizard closes. Click Close.
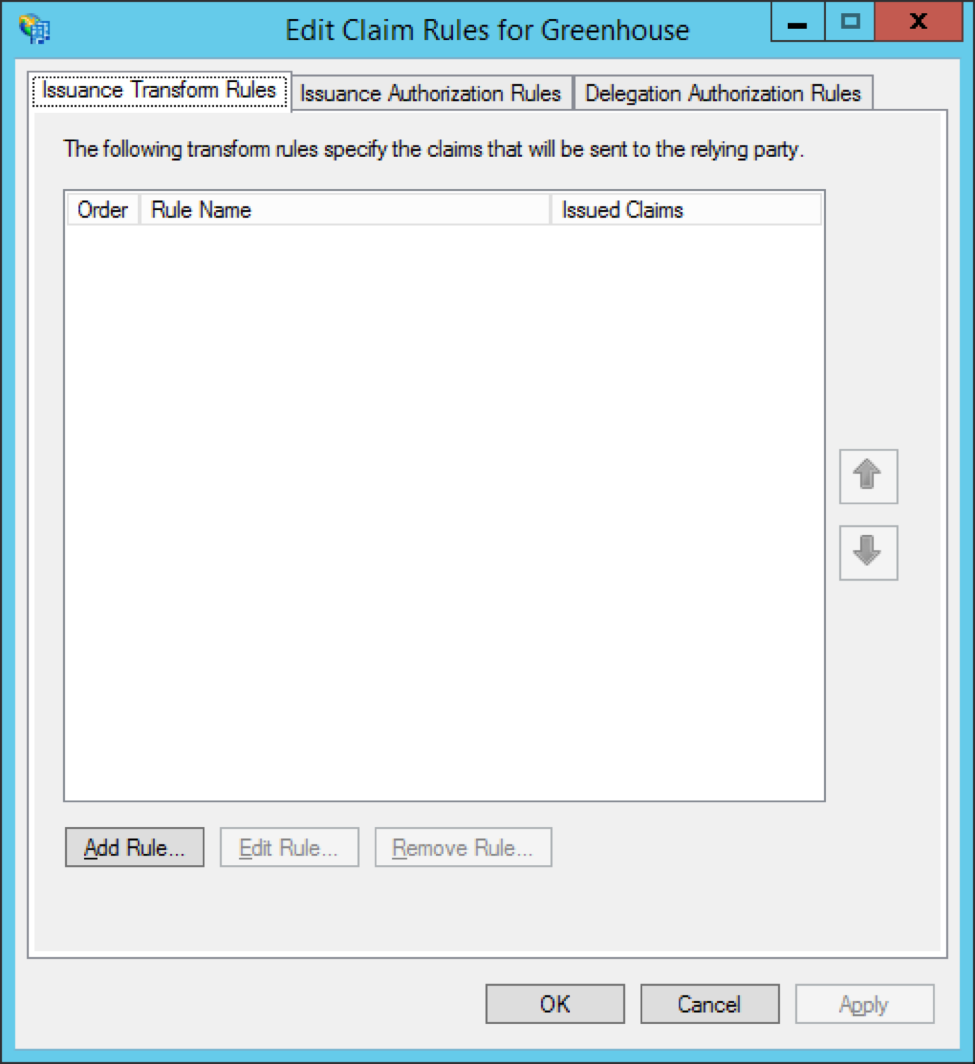
Step 2: Create claim rules for Greenhouse Onboarding
Closing the Add Relying Party Trust wizard automatically opens the Edit Claim Rules wizard for Greenhouse. Here, you'll configure the attributes that ADFS will send to Greenhouse Onboarding.
To begin, click Add Rule.
Select Send LDAP Attributes as Claims from the dropdown menu. Click Next.
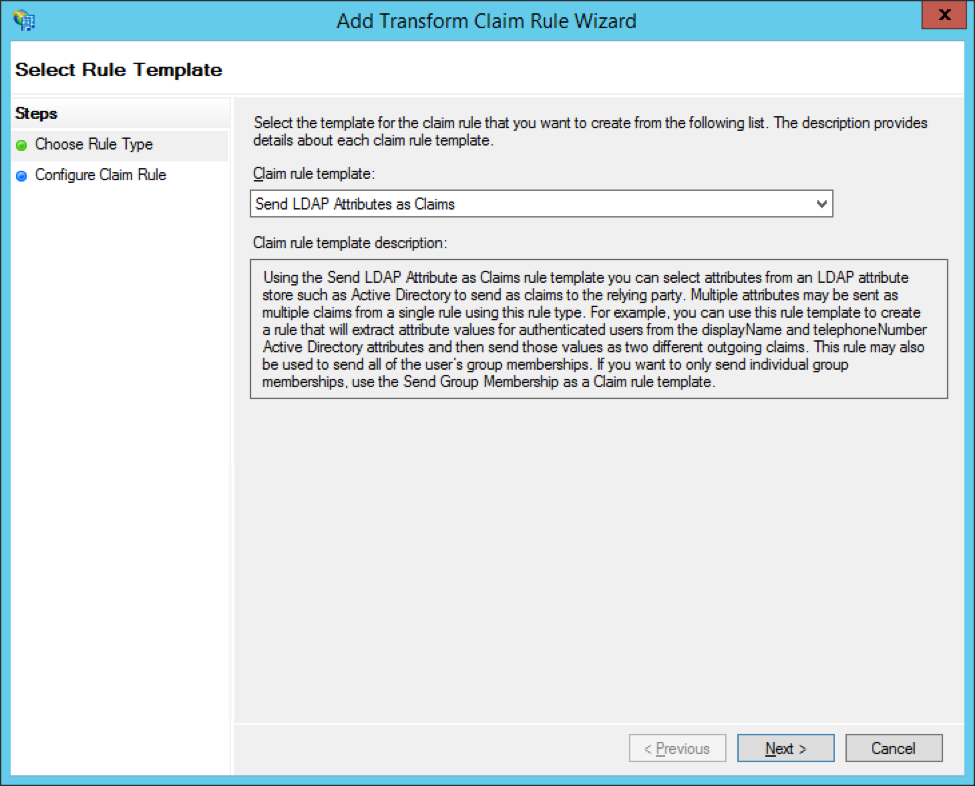
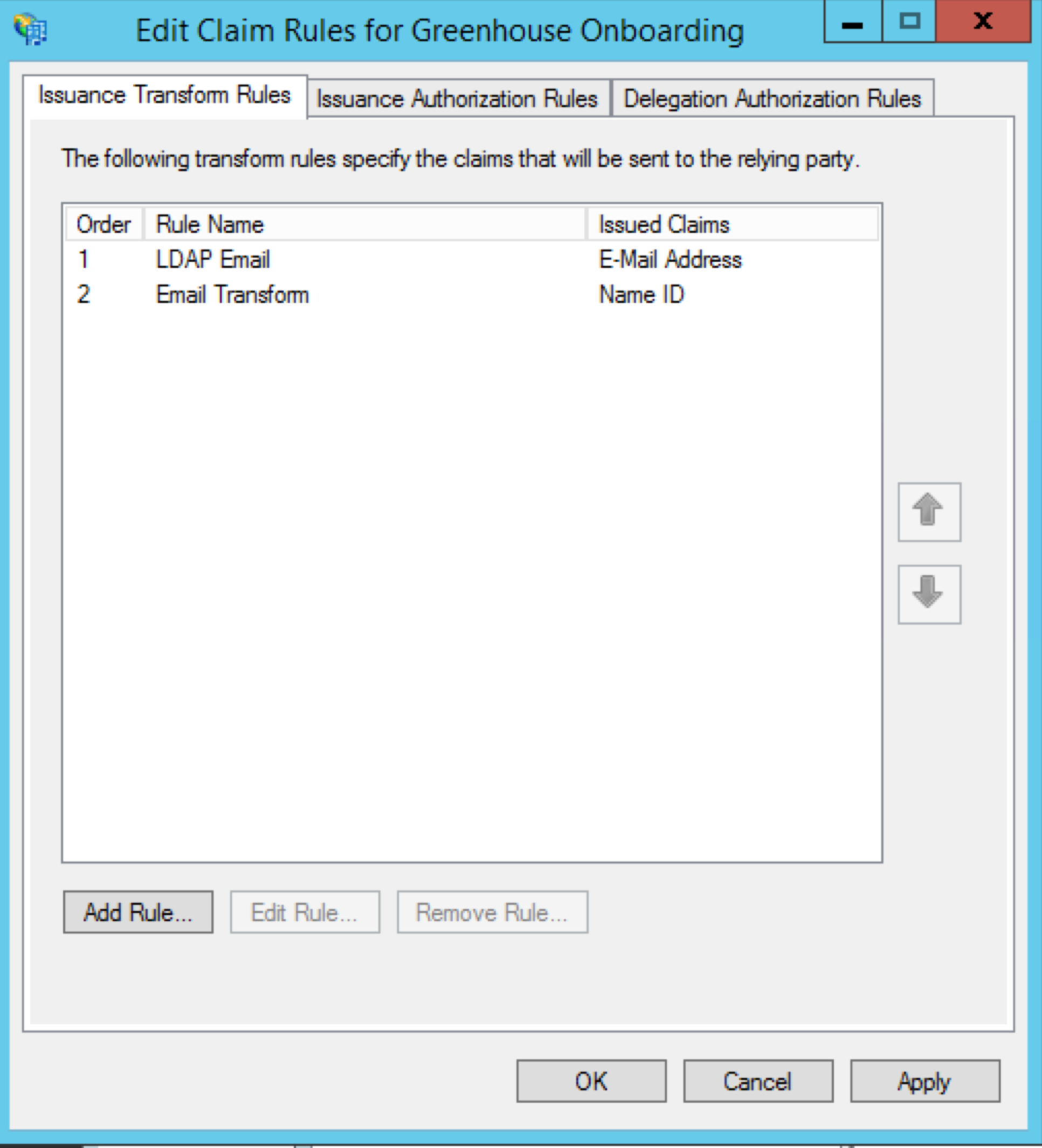
Name the claim rule LDAP Email and select Active Directory from the Attribute store dropdown menu.
Add the following rules under Mapping of LDAP attributes to outgoing claim types:
- Select E-Mail-Addresses in the LDAP Attribute column
- Select E-Mail Address in the Outgoing Claim Type column
Click Finish.
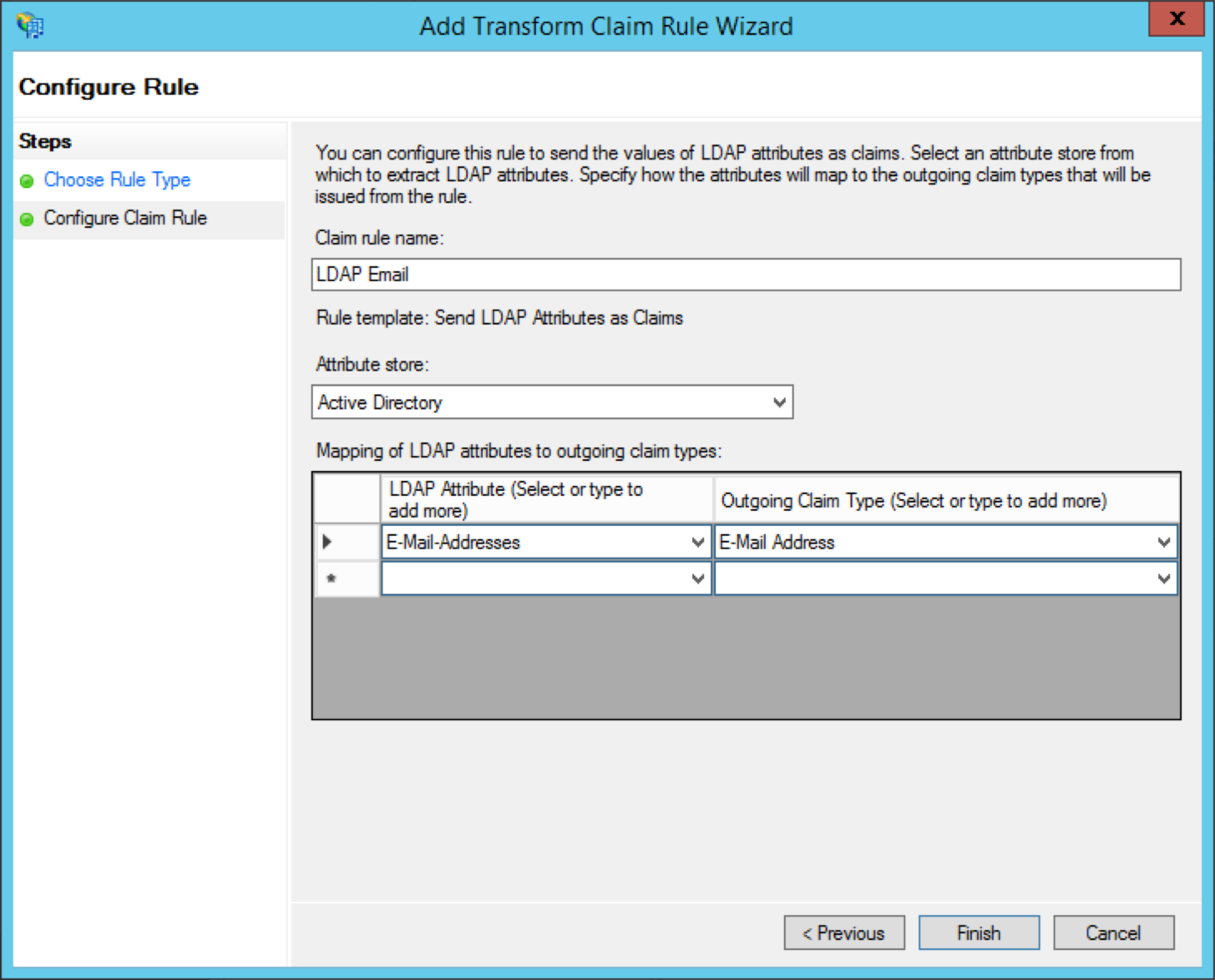
You'll now see the new rule in your list of claim rules for Greenhouse Onboarding.
Click Add Rule again to add another rule.
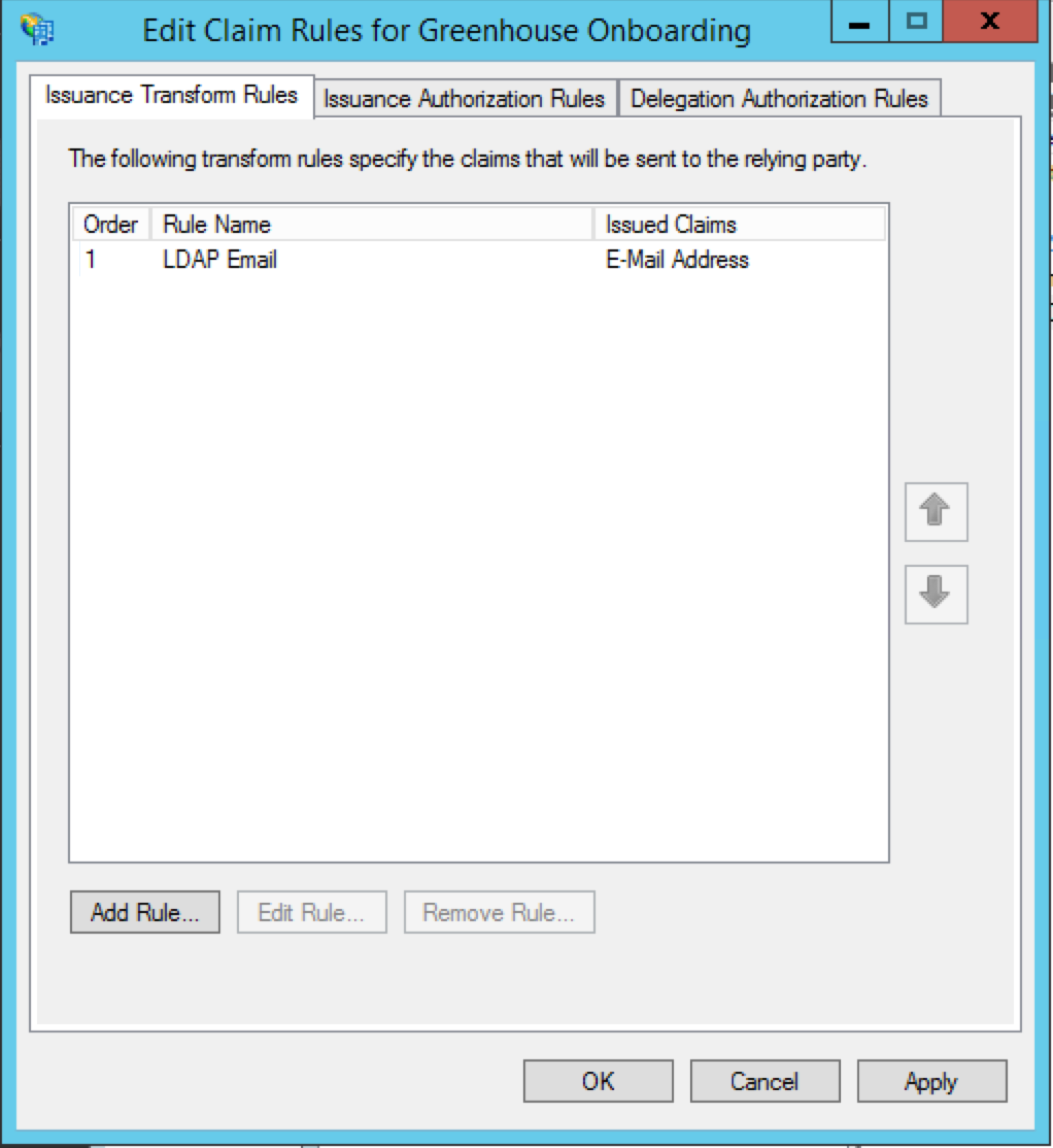
Select Transform an Incoming Claim from the dropdown menu. Click Next.
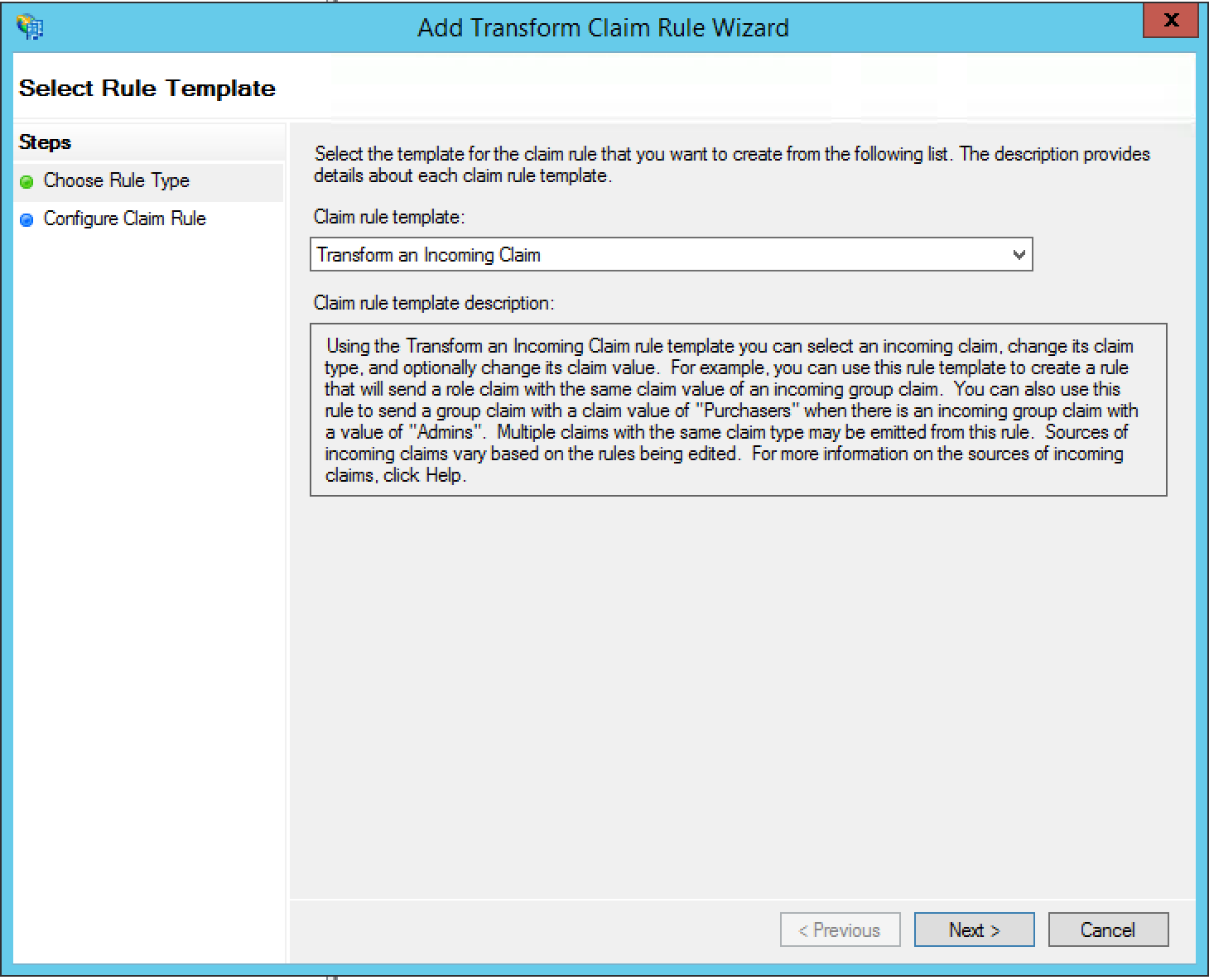
Configure the following settings on the next page:
- Set your Claim rule name to Email Transform
- Set the Incoming claim type to E-Mail Address
- Set the Outgoing claim type to Name ID
- Set the Outgoing name ID format to Email
- Select Pass through all claim values
Click Finish.
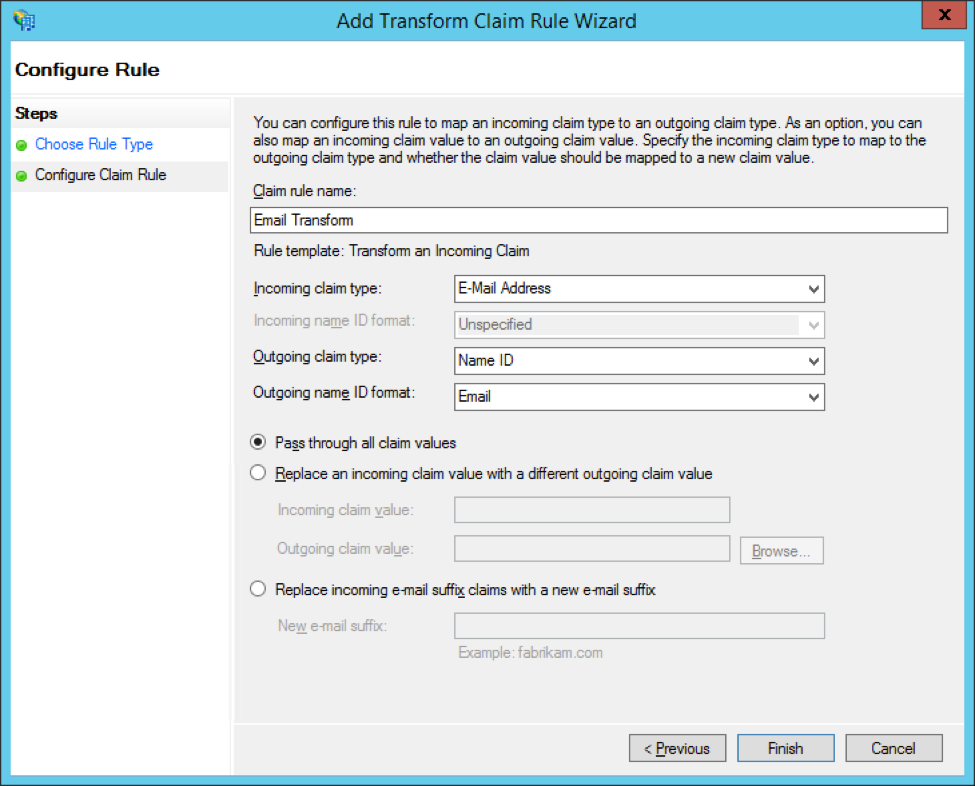
You'll now see both of your new rules in the list of claim rules for Greenhouse Onboarding.
Click Apply, then click OK to close the wizard.
Step 3: Edit the trust settings
The next step is to edit the trust settings for Greenhouse Onboarding.
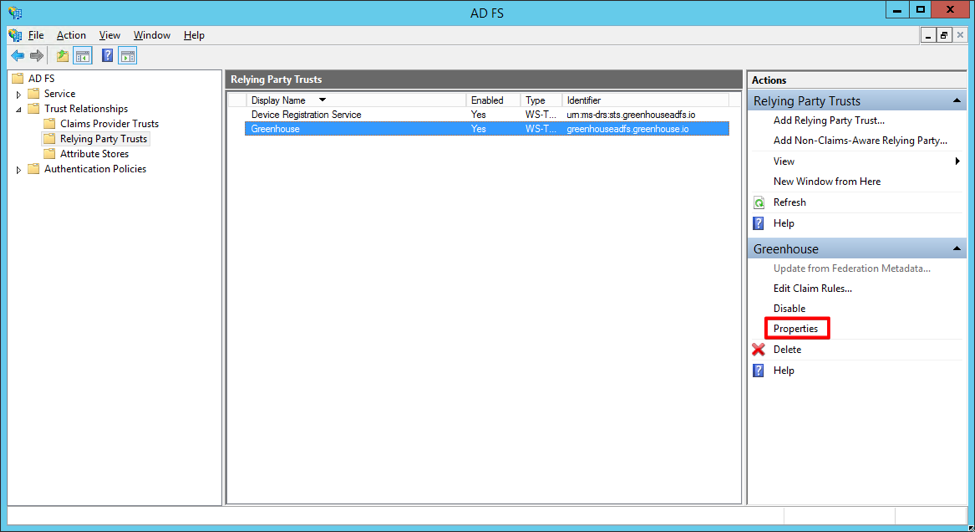
On the Relying Party Trusts page of your ADFS management tool, select Greenhouse Onboarding from the list of Relying Party Trusts.
In the Actions panel on the right, click Properties.
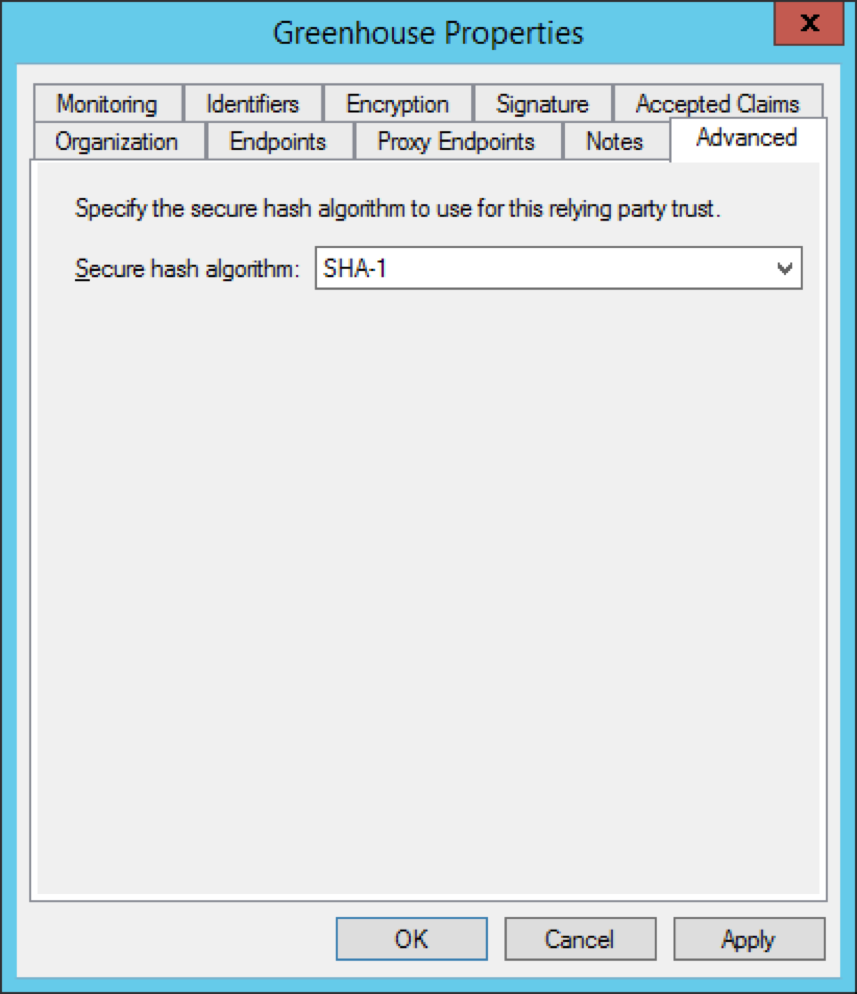
In the Greenhouse Properties window, navigate to the Advanced tab.
Set Secure hash algorithm to SHA-1 from the dropdown menu. Click OK.
Step 4: Set the NotBeforeSkew parameter
When a user logs in to Greenhouse Onboarding through ADFS, the SAML response to Greenhouse Onboarding will contain NotBefore and NotOnOrAfter attributes. These attributes designate the timeframe that the SAML Response is valid.
However, the ADFS server clock and the Greenhouse Onboarding server clock may become out of sync. In this case, the SAML Response will not be valid, which will prevent you from being able to log in.
To ensure that your users aren’t affected by server synchronization issues, set a skew of at least two minutes on the NotBefore attribute by following the below instructions:
To begin, open your PowerShell in ADFS.
Next, check the current NotBeforeSkew by running the following command in PowerShell: Get-ADFSRelyingPartyTrust –identifier “app.parklet.co
In the PowerShell response, scroll to the attribute NotBeforeSkew. The number next to the NotBeforeSkew is the current time of that attribute in minutes.
![]()
Set the NotBeforeSkew attribute to 2 minutes by running the following command in PowerShell: Set-ADFSRelyingPartyTrust –TargetIdentifier “app.parklet.co" –NotBeforeSkew 2
Check the new NotBeforeSkew by running the following command again: Get-ADFSRelyingPartyTrust –identifier “app.parklet.co
![]()
The NotBeforeSkew should now be set to 2.
Step 5: Configure a single logout URL (optional)
The final step is to configure a single logout URL.
Note: This step is optional.
On the Relying Party Trusts page of your ADFS management tool, select Greenhouse Onboarding from the list of Relying Party Trusts.
In the Actions panel on the right, click Properties.

Navigate to the Endpoints tab. You'll see your SSO Assertion Consumer URL from Greenhouse Onboarding in the list of endpoints.
To add a single logout URL, click Add SAML.
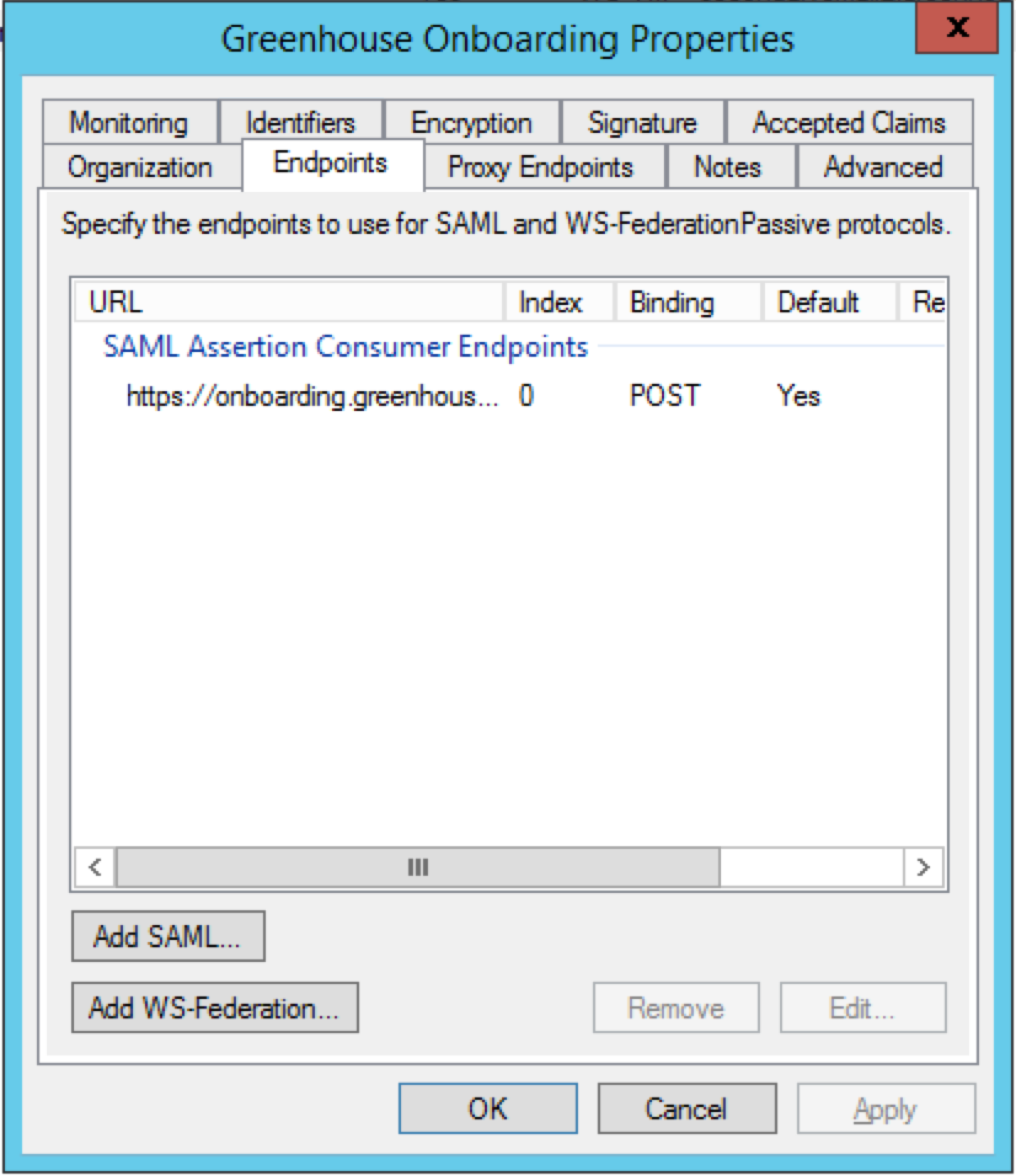
In the Add an Endpoint window, configure the following settings:
- Set the Endpoint type to SAML Logout
- Set Binding to POST
- In the Trusted URL textbox, enter your single logout URL.
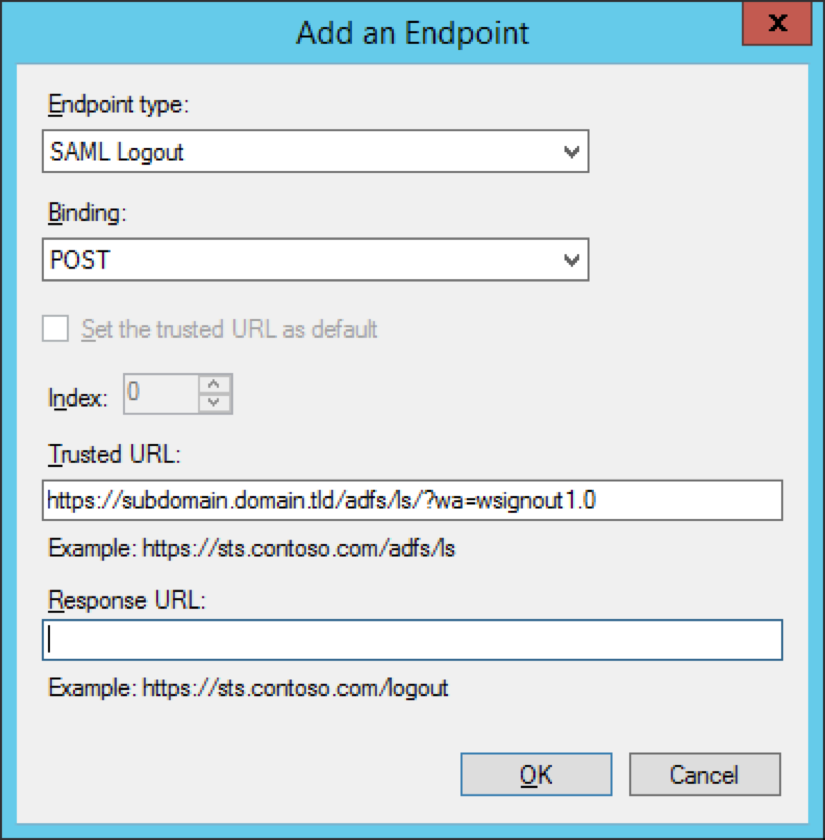
Your single logout URL will now appear on your list of endpoints for Greenhouse Onboarding.
Click Apply, then click OK.